Inspecting App Traffic
Recently I wrote an article talking about inspecting traffic between the app for a game that I play and it's server and writing an API library to cover it's undocumented "private" API. Today I want to dive deeper in to how this kind of thing is done to provide more of an understanding of the process.
Focusing specifically on mobile apps we can say that at a high level there are two components: the app and the backend. These two components are separate from each other and must communicate with each other over the interent. The typical way for this communication to happen is via HTTP requests where the app will send the backend a request and the backend will send a response. Both the request and response can contain data; it's easy to visualize thinking like a phone call where you are ordering food. You say "I want a large cheese pizza" (request) and the person on the other end replies "Okay that will be $20" (response). Since this communication happens over the internet it must bounce through several networks to get where it's going, starting with the network that your phone is connected to. I'm going to assume that you are connected to a home internet network, you should not do this on a network you don't own, although we will only be looking for your own traffic this could be considered illegal in some areas on public networks.
Using Network Tools (Proxyman)
The first step is to find the right tool for inspecting traffic you will want something that can setup a proxy for your local network so that you can connect your phone to it and show your phone's network traffic. This is like adding a third person to the phone call that can hear what is being said. There's a couple options that I know off hand one is Charles Proxy and the other, which I will use for this article is Proxyman. You could use more advanced tools like Wireshark for this as well but i'll skip those for now because these are far more user friendly.
Install Proxyman and launch it for the first time, you will be presented with a flow of network traffic from your own computer at first. On the left hand side you can see that Proxyman sorts these connections by app which is really helpful it will also sort your phone traffic into a section of it's own once we connect it.
Next you want to go to the menu:
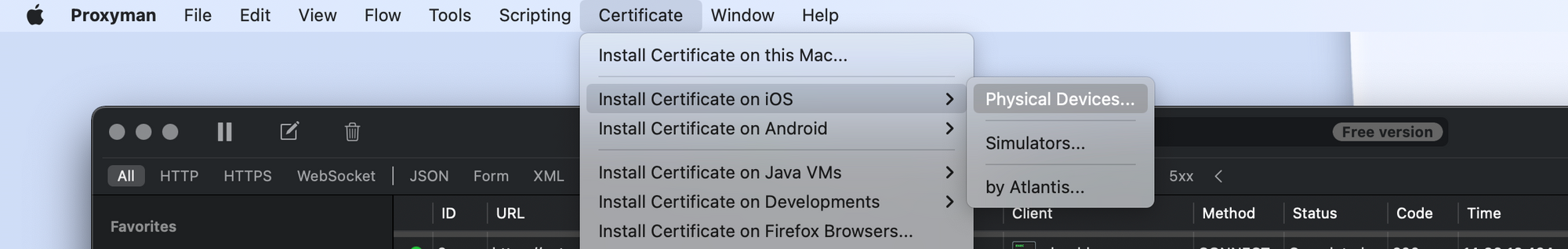
Certificate -> Install Certificate on iOS -> Physical Devices...Follow all of the steps in that pop up window to connect your device to Proxyman and install the certificates to your computer and your mobile device so that we can inspect HTTPS (SSL) traffic (more on that later). After doing this you will see a new section on the left hand side with your phone listed under "Remote devices"
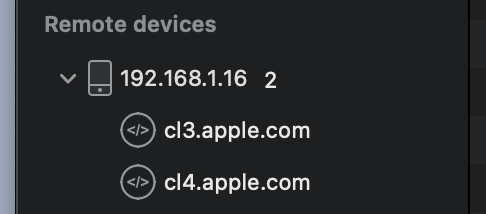
This section will include all of your phone's traffic as it communicates with the internet, sorted by host.
Identifying Target Traffic
Since Proxyman sorts traffic by host you can usually quickly identify the traffic you're looking for, as an example when I was debugging the Grepolis app I looked for domains containing grepolis.com which included two different subdomains en0.grepolis.com and en45.grepolis.com I needed traffic for both of these to do what I needed to do but it was clear which domains I should be watching. Usually the host is named after the app name or at least is usually the same as the domain name for the website for example Facebook and facebook.com. Once you have identified the host(s) which you want to inspect you can start clicking individual packets in the main list to see what's inside them. You will want to keep an eye on the Method column because we likely only care about POST, GET, UPDATE and DELETE requests.
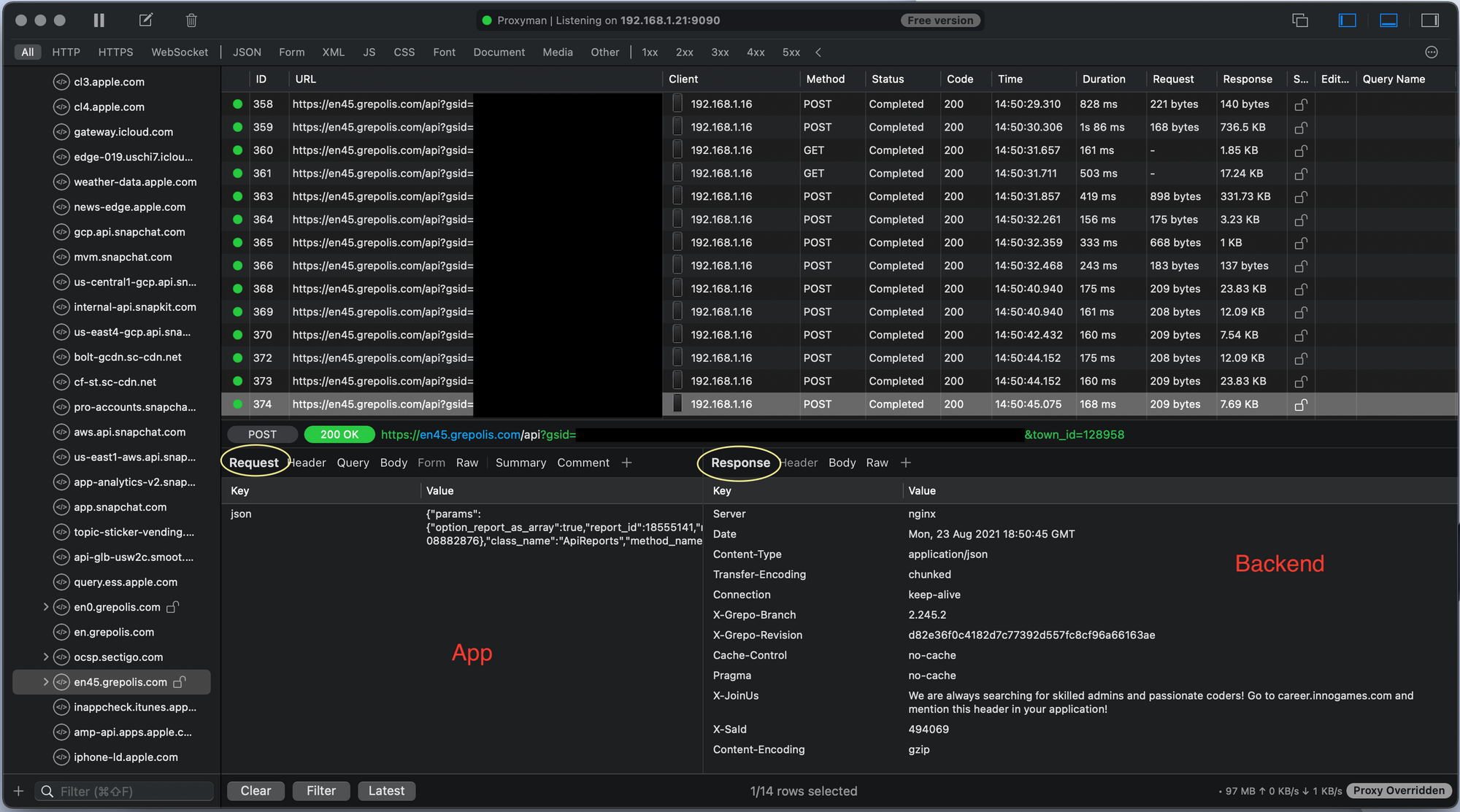
Decrypting HTTPS (SSL) Traffic
During the first couple steps when connecting your device to Proxyman you installed two certificates one on your local machine and one on your mobile device, what these certificates do is allow your computer to see the raw unencrypted data inside of the encrypted HTTPS (SSL) packets. HTTPS is designed to secure your traffic from this exact thing so by doing this you have effectively defeated a security measure designed to protect your data but only so that you can see it. This is called a Man in the Middle MitM attack which are very common on public networks so be careful! For this use it works perfectly because the use of HTTPS by platforms is very common now but our goal is to see what's inside of the traffic that our mobile device is sending and receiving.
Summary
Using this process you can watch all traffic on your personal computer, mobile devices and more. It's a very powerful tool that gives you a deeper understanding of what's going on on all your devices and your local network. Please keep in mind that you should only do this on devices and networks that belong to you. It is possible to do this to others however it's illegal and can get you in real legal trouble.




